Managed IT Services
Managed IT Services Done Right.
Managed IT Services Done Right.
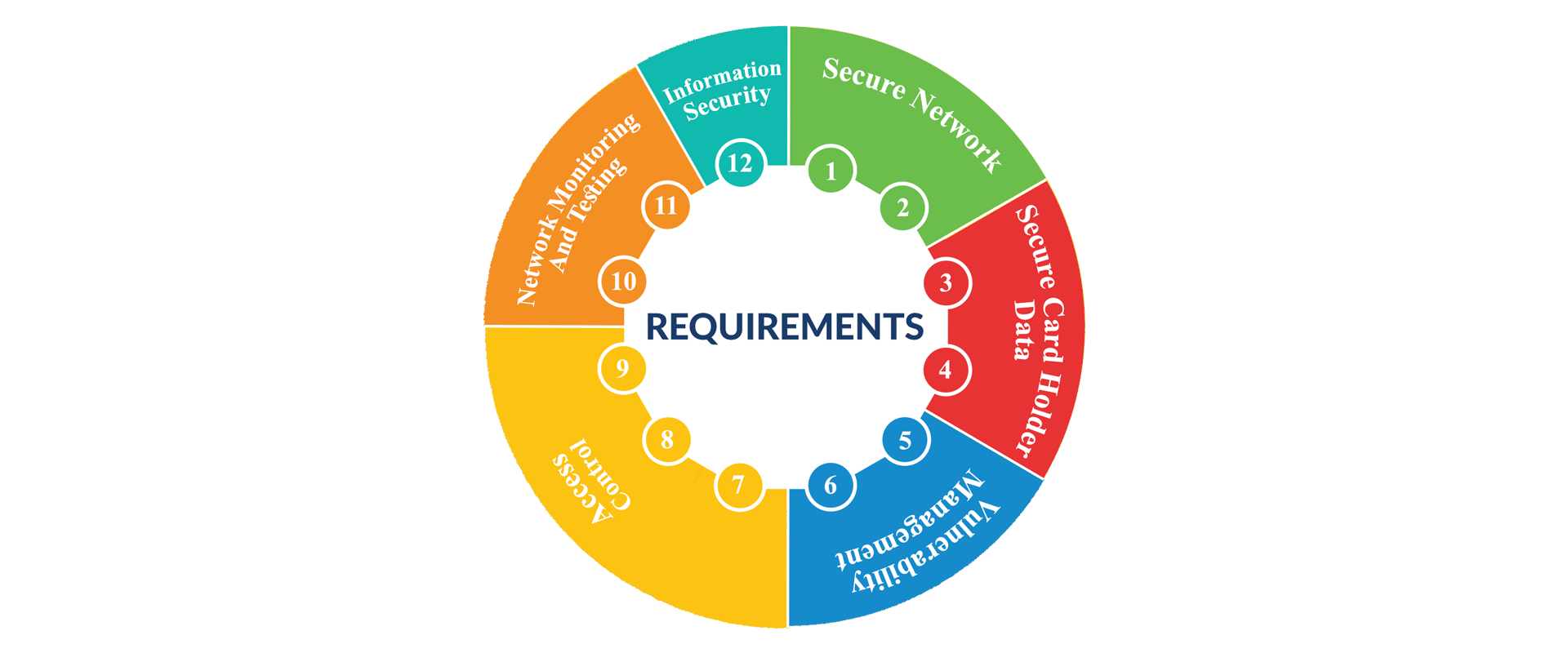
Zebra Security provides specialized security services to businesses and organizations which may include mixture of the following:
- Monitoring: Monitoring clients networks and systems for any security threats or vulnerabilities. This can include monitoring for malware, hacking attempts, and other malicious activity.
- Incident response: Responding to security incidents and breaches on behalf of their clients. This can include identifying the cause of the incident, containing the damage, and restoring systems to normal operations.
- Compliance: Ensuring that clients networks and systems are compliant with relevant security regulations and standards, such as HIPAA, PCI-DSS, and others.
- Risk assessment: Assessing clients security risks and vulnerabilities, and recommending appropriate countermeasures to mitigate those risks.
- Reporting: Providing clients with regular reports on their security status, including any incidents, vulnerabilities, or other issues that have been identified.
- Training: Training and education to clients staff on how to identify and prevent security threats, as well as incident response procedures.
- Managed Security services: Providing comprehensive security services to their clients, including threat management, vulnerability management, intrusion detection and prevention, and security event management.
Overall, Zebra Security can assist businesses managing and protecting the security of networks and systems, while also ensuring compliance with relevant regulations and standards. They also provide an extra layer of protection and support to their clients, allowing them to focus on their core business operations.